| Desarrollador: | Gatelink Ltd (8) | ||
| Precio: | $84.99 | ||
| Clasificaciones: | 5 (1) | ||
| Opiniones: | 0 Escribir una opinión | ||
| Listas: | 0 + 0 | ||
| Puntos: | 0 + 0 ¡ | ||
| Puntos + 1 | |||
Descripción

The application allows the following actions:
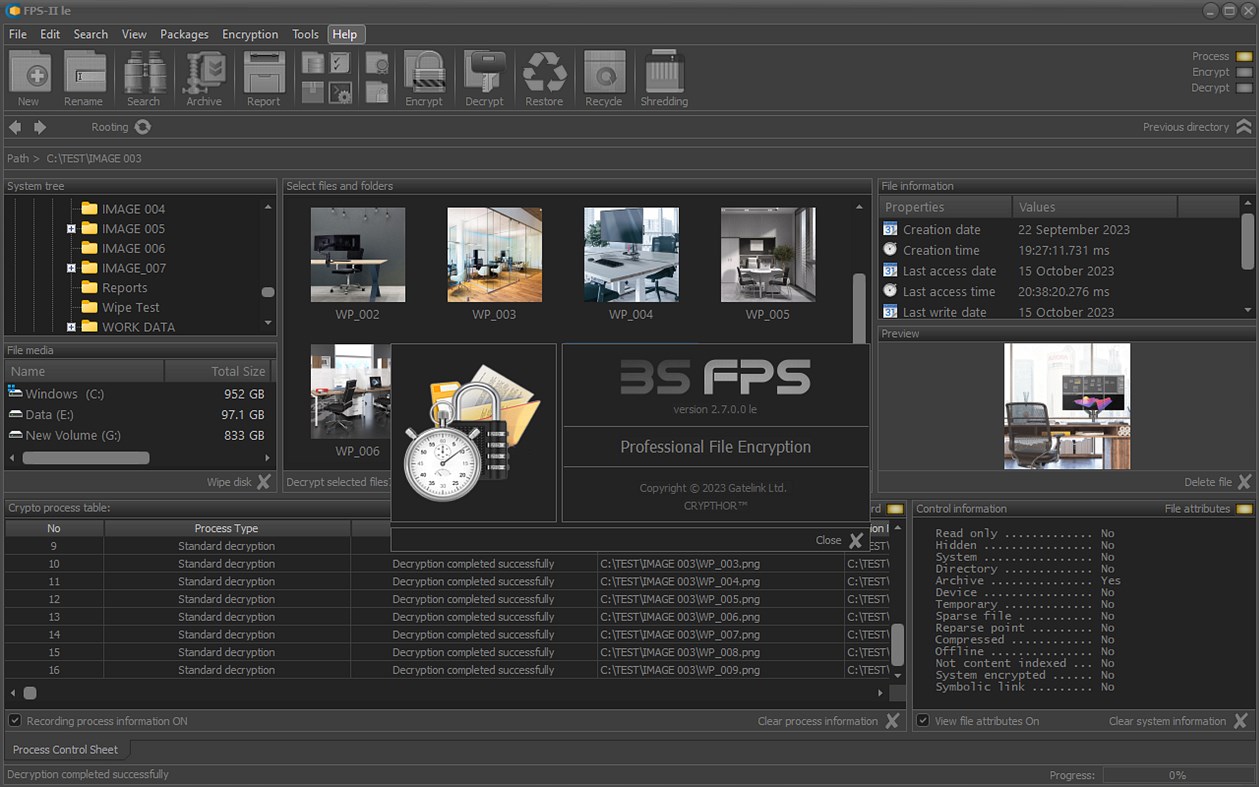
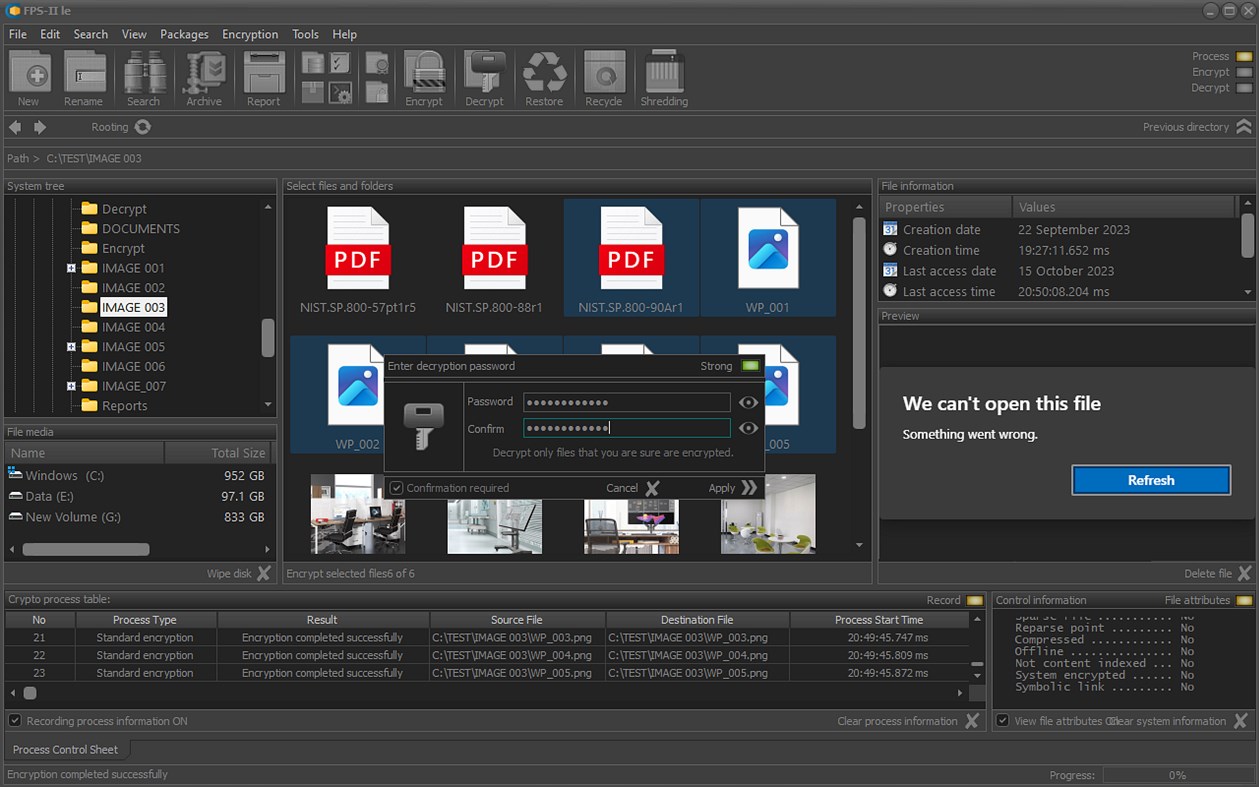
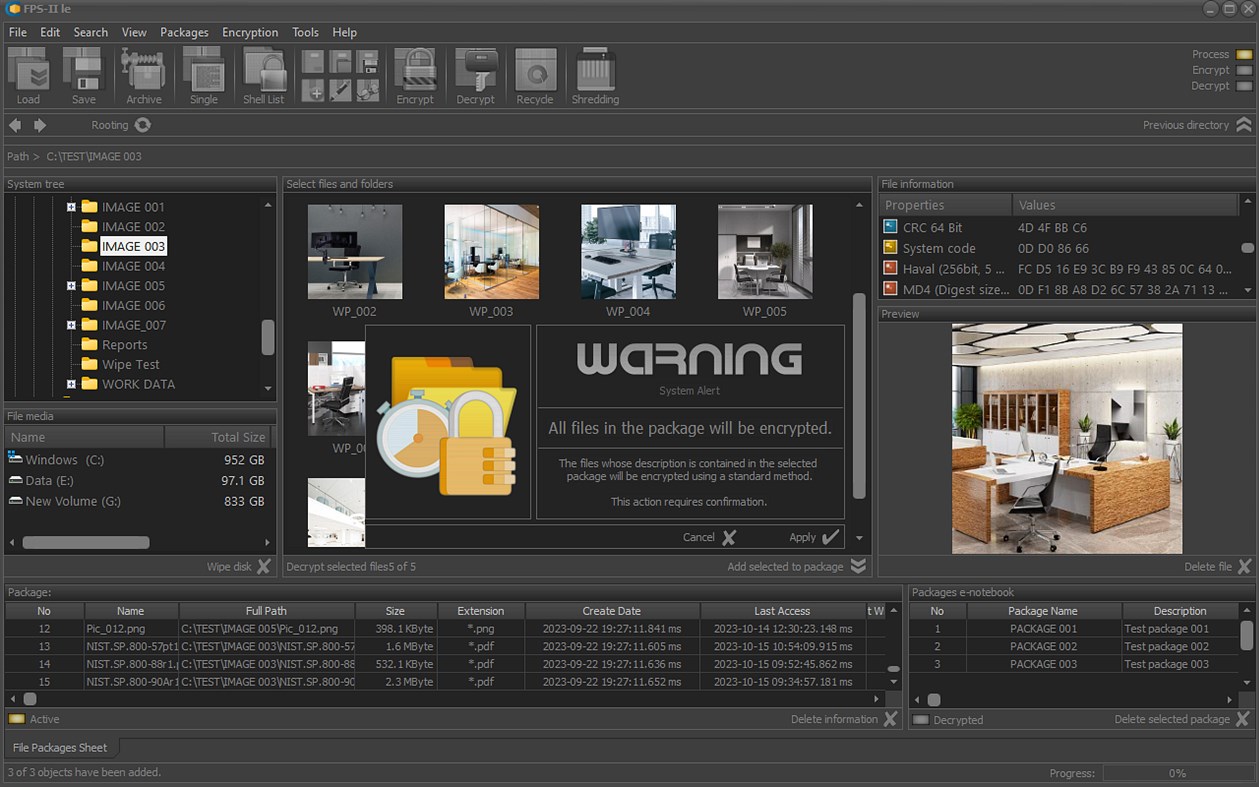
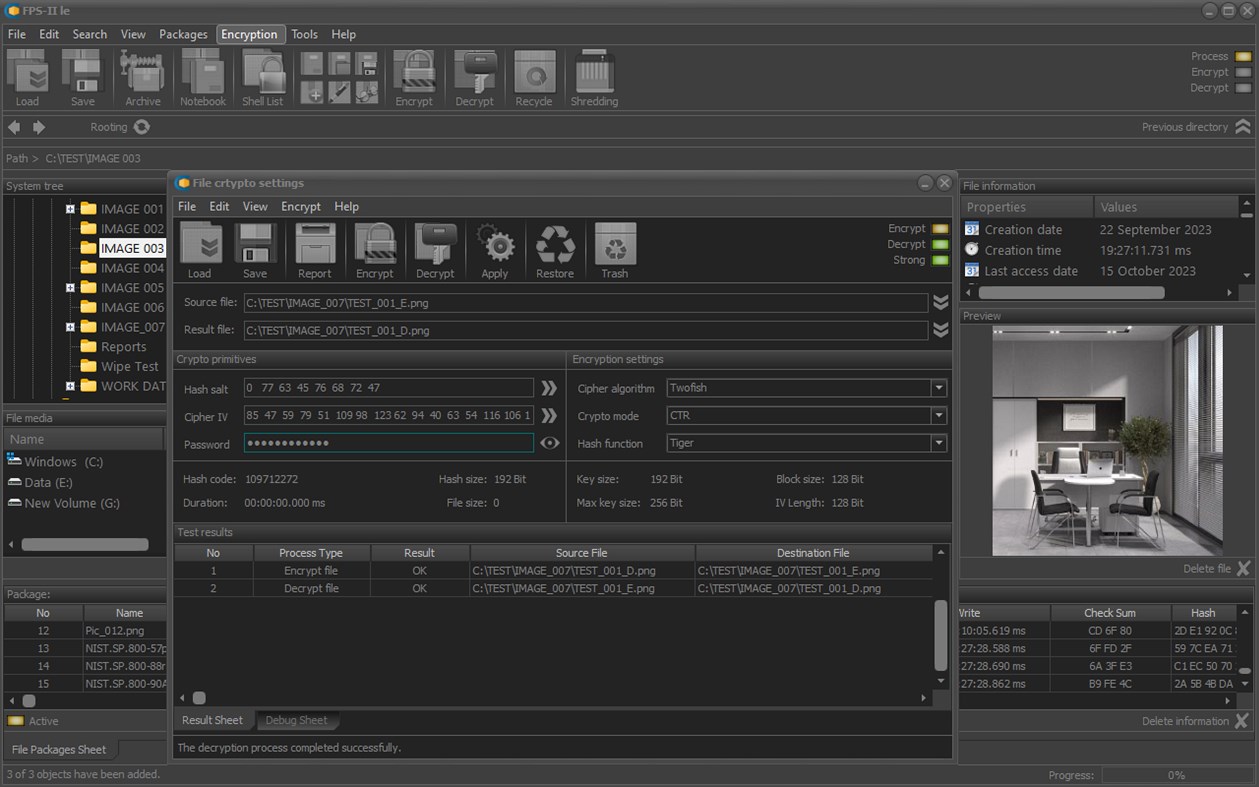
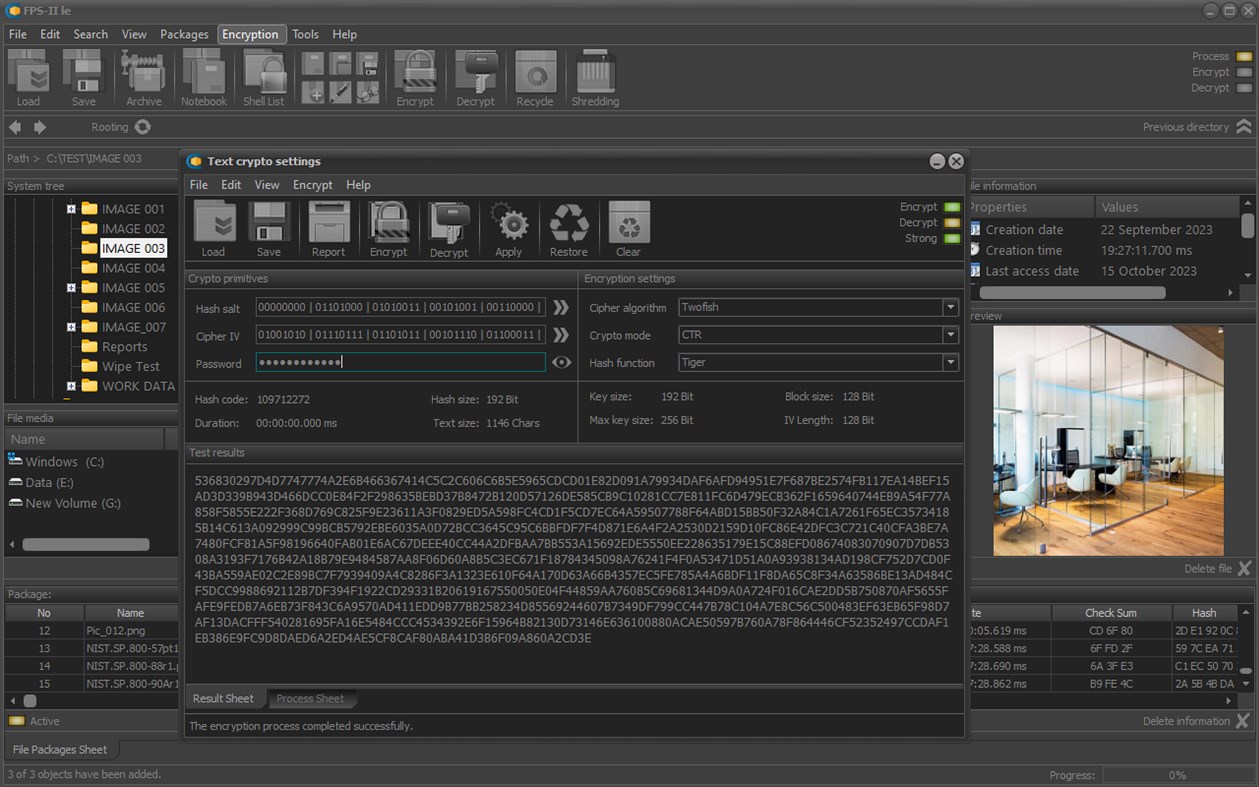
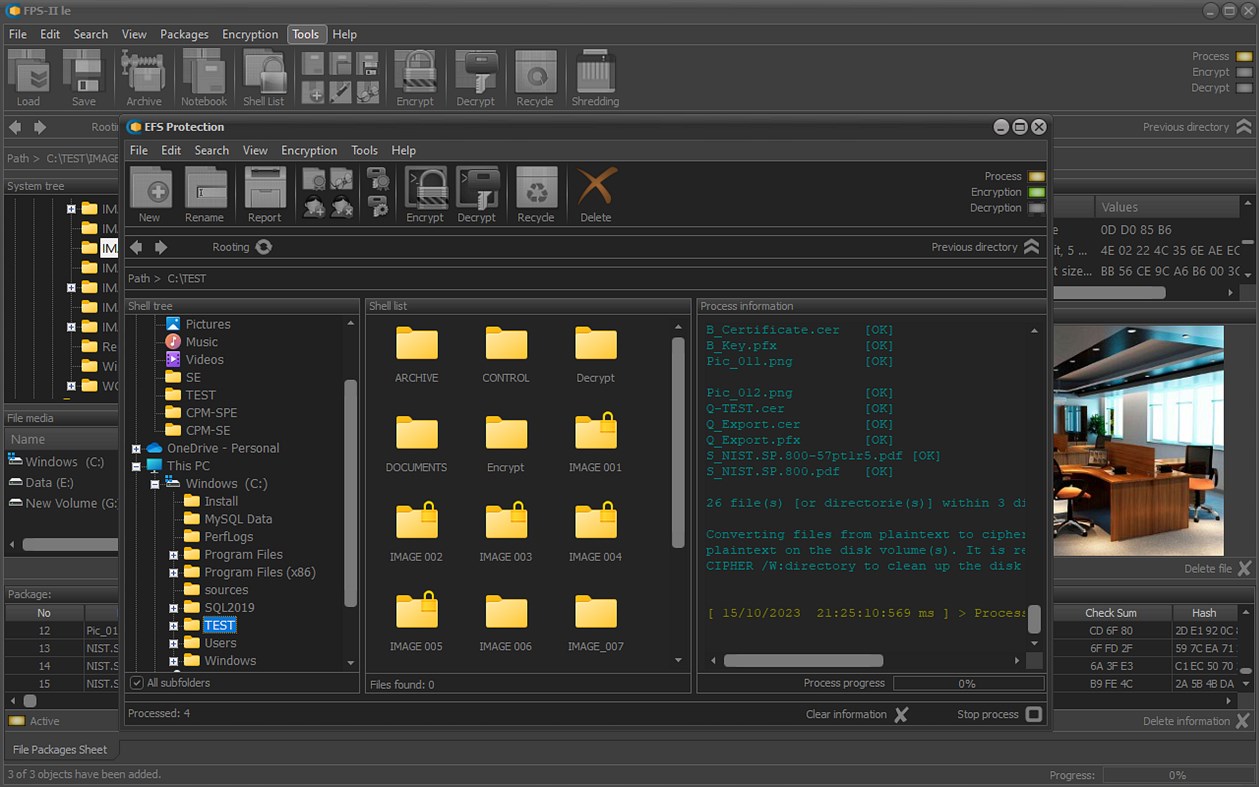
• Encrypt or decrypt selected files and folders;
• Management of the cryptographic primitives used;
• Storing the used primitives in secure electronic notebooks;
• Management of delta cryptographic primitives (implicit security primitives, ISP);
• Formation of session secret keys based on randomly selected delta primitives (CDP encryption);
• Recording the critical information in implicit security form.
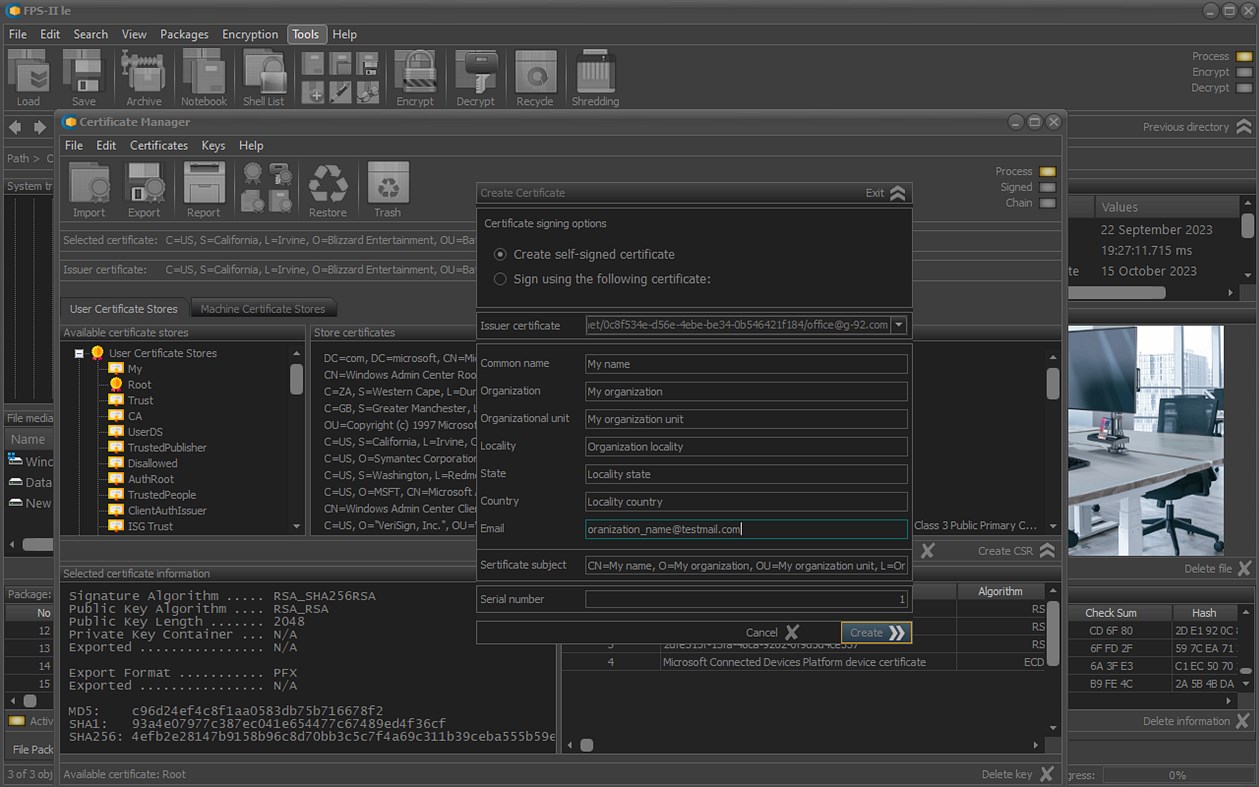
• Management of digital certificates (generation, export, signing, etc.);
• Secure electronic notebooks for storing digital certificates and secret keys;
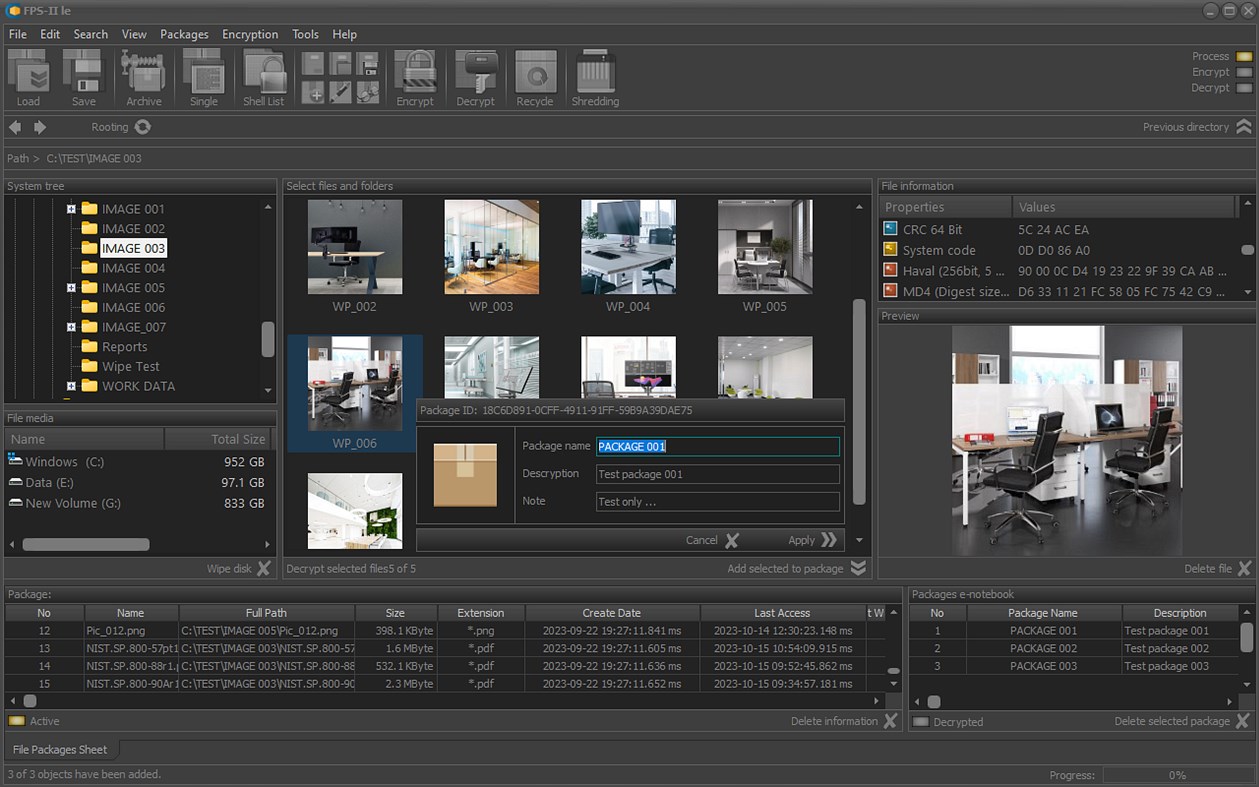
• Management of cryptographic processes for file packages;
• Design and implementation of meta scenarios for the protection of digital data;
• Real-time processes control;
• Automatic formation of official reports;
• Management of the processes related to the destruction of critical information, etc.
FIELD OF APPLICATION
Protecting large arrays of files located on different media is a complex and difficult process to perform.
Procedures related to the storage, editing, transfer, and destruction of files are of utmost importance to ensure compliance with security protocols during the exploitation cycle.
Statistics show that most unauthorized access attempts aim at the critical information in specific files, including the authentication certificates used.
FPS enables the maximum reduction of risks by using a set of highly effective professional solutions to protect both specific groups of files and any information located on data storage devices
The application uses some of the most effective standard encryption algorithms used by government organizations and corporate structures.
The module for the formation of service reports makes the application an indispensable tool when building cyber security systems that meet the requirements of ISO - ISO/IEC 27001 and ISO - ISO/IEC 27002.
The development process used both standard algorithms described in NIST SP 800-88 and NIST SP 800-90A, which include Hash DRBG (based on a hash function), HMAC DRBG (based on HMAC), and CTR DRBG (based on block ciphers in counter mode), as well as some specific solutions used in the technology BS 1443, BS 7122, etc.
TECHNOLOGICAL SOLUTIONS
The correct choice of algorithms and software technologies for digital data encryption is a guarantee of the high efficiency and reliability of the application.
The application uses a set of standard and modified algorithms for encrypting mechanisms.
The following standard algorithms are used in the base versions:
STANDARD ENCRYPTION ALGORITHMS
(basic technologies)
• Blowfish
• CAST-128 [ CAST-5 ]
• CAST-256 [ CAST-6 ]
• Data Encryption Standard [ DES ]
• Triple DES [ 3DES ]
• Information Concealment Engine [ ICE ]
• Thin-ICE [Information Concealment Engine]
• Information Concealment Engine 2 [ ICE-2 ]
• IDEA [ PGP ]
• MARS
• MISTY1 [ MISTY-1 ]
• Ron’s Code or Rivest’s Cipher 2 [ RC-2 ]
• Ron’s Code or Rivest’s Cipher 4 [ RC-4 ]
• Ron’s Code or Rivest’s Cipher 5 [ RC-5 ]
• Ron’s Code or Rivest’s Cipher 6 [ RC-6 ]
• Advanced Encryption Standard [ AES, Rijndael ]
• Serpent
• Tiny Encryption Algorithm [ TEA ]
• Twofish
AFFORDABLE HASH FUNCTIONS
(basic technologies)
• Haval [ 256 Bit, 5 passes ]
• Message Digest 4 [ MD-4 ]
• Message Digest 5 [ MD-5 ]
• RIPEMD-128
• RIPEMD-160
• Secure Hash Algorithm 1 [ SHA-1 ]
• SHA-256 [ SHA-2 family ]
• SHA-384 [ SHA-2 family ]
• SHA-512 [ SHA-2 family ]
• Tiger
STANDARD ENCRYPTION MODES
(basic technologies)
• CBC (Cipher Block Chaining)
• CFB (Cipher Feedback)
• CFB8 (Cipher Feedback 8)
• CTR (Counter Mode )
• OFB (Output Feedback Mode)
The available hybrid solutions for the non-special purpose versions are as follows:
SPECIAL ALGORITHMS
(hybrid technology)
• BS Standard Protection Mode (SPM) - Crypto-mechanisms are generated by using specialized control panels. Each of these crypto mechanisms uses a set of cryptographic primitives that can be session-based or stored in highly secure digital containers.
BS Package Protection Mode (PPM) - The crypto mechanisms used are common to each of the files, information about which is contained in the file package. In case of need, individual elements of the crypto mechanisms can be hardware dependent or be tied to the use of control strings.
• BS Hybrid Protection Mode (HPM) - In this case, each of the files in the package is encrypted using a session crypto mechanism, which is formed based on the information in the electronic notebook and the specialized areas in the control strings. In addition, individual elements of the meta-information about the files and folders stored in the package are used.
ACCORDANCE WITH ACCEPTED STANDARDS:
• ISO 10116: Information Processing - Modes of Operation for an n-bit block cipher algorithm.
• ISO 9797: Data cryptographic techniques - Data integrity mechanism using a cryptographic check function employing a block cipher algorithm.
• ISO 9798-2: Information technology - Security techniques - Entity authentication mechanisms - Part 2: Entity authentication using symmetric techniques.
• ISO 10118-2: Information technology - Security techniques - Hash-functions - Part 2: Hash-functions using an n-bit block cipher algorithm.
• ISO 11770-2: Information technology - Security techniques - Key management - Part 2: Key management mechanisms using symmetric techniques.
• FIPS 140 - Federal Information Processing Standard (FIPS) 140-2, Security Requirements for Cryptographic Modules, May 25, 2001
(including Change Notices as of December 3, 2002).
• FIPS 180 - Federal Information Processing Standard (FIPS) 180-4, Secure Hash Standard (SHS), March 2012.
• FIPS 197 - Federal Information Processing Standard (FIPS) 197, Advanced Encryption Standard (AES), November 2001.
• FIPS 198 - Federal Information Processing Standard (FIPS) 198-1, The Keyed-Hash Message Authentication Code (HMAC), July 2008.
• SP 800-38D - National Institute of Standards and Technology Special Publication (SP) 800-38D, Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC, November 2007.
• SP 800-57 - NIST Special Publication (SP) 800-57 Part 1 Revision 3, Recommendation for Key Management - Part 1: General, July 2012.
• SP 800-90B - NIST Special Publication (SP) 800-90B (Draft), Recommendation for the Entropy Sources Used for Random Bit Generation, August 2012.
• SP 800-90C - NIST Special Publication (SP) 800-90C (Draft), Recommendation for Random Bit Generator (RBG) Constructions, August 2012.
• SP 800-107 - NIST Special Publication (SP) 800-107 Revision 1, Recommendation for Applications Using Approved Hash Algorithms, August 2012 etc.
Novedades
- Versión: PC
- Actualizado:
Precio
- Hoy: $84.99
- Mínimo: Gratis
- Máximo: $84.99
Realizar un seguimiento de los precios
Desarrollador
- Gatelink Ltd
- Plataformas: Windows Aplicaciones (8)
- Listas: 0 + 0
- Puntos: 2 + 5 ¡
- Clasificaciones: 5 (3)
- Opiniones: 5 (2)
- Descuentos: 0
- Vídeos: 0
- RSS: Suscribirse
Puntos
No encontrada ☹️
Clasificaciones
-

- 35 Semes
- 5
Listas
No encontrada ☹️
Opiniones
Sé el primero en escribir una reseña!
Información adicional
Contactos
- Sitio:
http://fps.g-92.com
También te puede interesar
-
- File Protect System
- Windows Aplicaciones: Seguridad De: Gatelink Ltd
- * Gratis
- Listas: 0 + 0 Clasificaciones: 5 (1) Opiniones: 5 (1)
- Puntos: 0 + 3 Versión: PC File Protect System (version FPS-II se) is a specialized, hybrid application for managing the life cycle of critical information that is stored on local or server data devices. The ...
-
- File Protect System - C
- Windows Aplicaciones: Seguridad De: GEYA-92 OOD
- $19.99
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 0 Versión: PC File Protect System (FPS Client) is a software application for protection of personal data and critical information. This protection is performed by reliable strong encryption of files
-
- File Encryptor Pro
- Windows Aplicaciones: Seguridad De: App-Ink.NET
- Gratis
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 1 Versión: PC Store or send your files with sensitive content encrypted. This software encrypts any file format using AES. This application is also available as a webapp ...
-
- File Locker X - Password Protect Files
- Windows Aplicaciones: Seguridad De: IO Stream Co., Ltd
- $4.99
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 11 Versión: PC Password-protect files and folders to secure your sensitive data and decrypt your data back easily. Encrypt and decrypt multiple files or folders at once. There's no limit to how many ...
-
- File Privacy
- Windows Aplicaciones: Seguridad De: Needed Special Tools
- Gratis
- Listas: 1 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 3 + 2 Versión: PC 3DES is one of the most prominent forms of encryption and has a symmetric-key block cipher algorithm. File Privacy uses Triple DES (3DES or TDES). You encrypt your files using the key ...
-
- File Scrubber
- Windows Aplicaciones: Seguridad De: R E Janisch
- $1.99
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 0 Versión: PC A simple App to scrub personal data from no longer needed files. App will over write your data from 10 to 15 times with random data before deleting the file. If a hacker is able to ...
-
- File Secure
- Windows Aplicaciones: Seguridad De: Rapid Technologies Pakistan
- Gratis
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 3 Versión: PC Encrypt your files with password. This application allows you to encrypt your data with password to avoid publicising.
-
- Paranoia File Encryption & Text Encryption PRO
- Windows Aplicaciones: Seguridad De: Paranoia Works
- $3.49
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 2 Versión: PC The application comprises two modules: File Encryptor: This module allows you to securely encrypt your private and confidential files or entire folders. You can accomplish the ...
-
- Secure File
- Windows Aplicaciones: Seguridad De: Area181 Software
- Gratis
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 1 Versión: PC Secure File will encrypt any file the user has access to on their system. It uses industry standard AES-256 for encryption. The key used to encrypt a file is randomly generated for ...
-
- CRYPTO File Encryption
- Windows Aplicaciones: Seguridad De: Levicom Inc.
- $0.99
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 1 Versión: PC CRYPTO File Encryption software by Levicom is a simple and easy to use file encryption and decryption software. Encrypts and password protect your files with an AES encryption ...
-
- 1LimX - Encrypted File, Password Manager
- Windows Aplicaciones: Seguridad De: Hahoto
- * Gratis
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 1 + 0 Versión: PC 1LimX Windows version 2 major changes: 1. Rich Text has arrived for creating secure, captivating and Intuitive messages, notes: 2. Templates, Categories up to 100 each used in items in
-
- Secure File Shredder
- Windows Aplicaciones: Seguridad De: Evlar
- $2.89
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 0 + 1 Versión: PC Did you know that when you delete files from your computer, they can still be recovered using special software? That creates a serious security risk from hackers that may access your ...
-
- Folder & File Lock
- Windows Aplicaciones: Seguridad De: MedhaChaitanya
- * Gratis
- Listas: 0 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 1 + 1,448 Versión: PC The folder and file protection software that you are waiting for is now here! I have completely re-worked on the app. Thank you for all the feedback and reviews for the initial ...
-
- DSE File Encryptor
- Windows Aplicaciones: Seguridad De: Data Safety Expert
- Gratis
- Listas: 1 + 0 Clasificaciones: 0 Opiniones: 0
- Puntos: 2 + 4 Versión: PC Professional file encryptor and decryptor. This app uses the best encryption algorithms available today: AES-128, AES-192 and AES-256. Optionally, this app can sign the encrypted file ...
También te puede interesar
- Windows Aplicaciones
- Nuevas Windows Aplicaciones
- Seguridad Windows Aplicaciones : Nuevas
- Vídeos Windows Aplicaciones
- Populares Windows Aplicaciones
- Seguridad Windows Aplicaciones : Populares
- Descuentos Windows Aplicaciones
- Seguridad Windows Aplicaciones : Descuentos
- Clasificaciones Windows Aplicaciones
- Opiniones Windows Aplicaciones
- Listas Windows Aplicaciones
- Puntos Windows Aplicaciones